
Configuring Fine-Grained Password Policies in Windows Server 2008 R2
Fine-Grained Password policies is a Long-Awaited Password and Account Policy Solution from Microsoft, which allow multiple password and account lockout policy settings to different sets of users in the same domain. Prior to Windows Server 2008/2008 R2, we have only a one password and account lockout policy, defined at the domain level. This limitation led complicated for many organizations. So some organizations “Disable Password must meet complexity requirements and Minimum password length” Domain policy in Active Directory Domain in Windows Server 2003. With Fine-Grained Password Policies in Windows Server 2008/2008 R2, we can create multiple password and lockout policies in the same domain. To configure a Fine-Grained Password Policy, the domain functional level must be at least Windows Server 2008/2008R2 and you must be a member of the Domain Admin Group to create PSOs (Password settings object). Fine-Grained Password Policies can only be applied to users or global security groups. PSOs can be created through ADSI Edit or LDIFDE.
To configure a Fine-Grained Password Policy, the domain functional level must be at least Windows Server 2008/2008R2 and you must be a member of the Domain Admin Group to create PSOs (Password settings object). Fine-Grained Password Policies can only be applied to users or global security groups. PSOs can be created through ADSI Edit or LDIFDE.
Here, we can create and apply a PSO to CashCounterPSO Group with the following group using adsiedit.msc.
1. Log on to DC, KTM-DC01, with a user account that is a member of Domain Admins group.
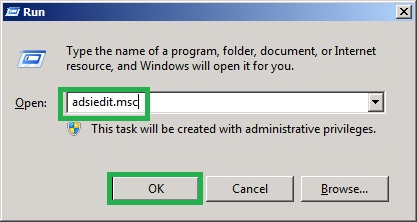
2. In the Run dialog box, type adsiedit.msc and Press Enter.
3. Right-click on ADSI Edit, and select Connect to …
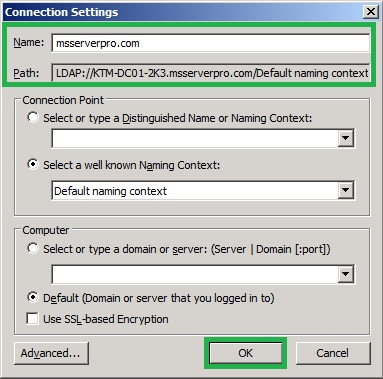
4. On the Connection Settings dialog box, type the fully qualified domain name of our domain, msserverpro.com and click OK.
5. Expand the ADSI Edit console until to locate the CN=Password Settings Container node and select New>Object…
6. In the Create Object dialog box, select msDS-PasswordSettings and click Next.
7. In the Create Object dialog box, type CashCounterPSO in the Value text box. This is the common name of the PSO and click Next.
8. In the Create Object, Password Settings Precedence page, type 10. Values greater than 0 are acceptable and click Next.
9. In the Create Object , Password Reversible Encryption Status for User Accounts page, type False and click Next. This password is not stored by using reversible encryption.
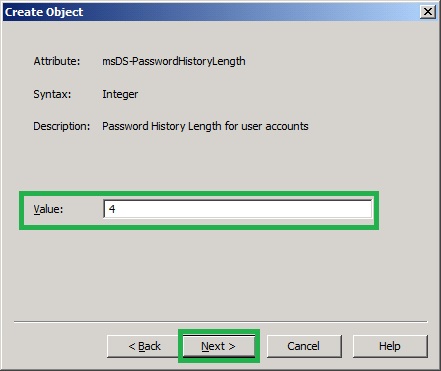
10. In the Create Object, Password History Length for User accounts page, type 4 and click Next. This user cannot reuse any of the last 4 passwords.
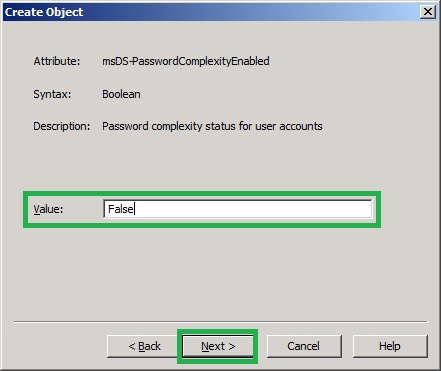
11. In the Create Object, Password complexity status for user accounts page, type False and click Next. Password complexity rules are disabled.
12. In the Create Object, Minimum password length for user accounts page, type 4 and click Next. Password must be at least 4 characters long.
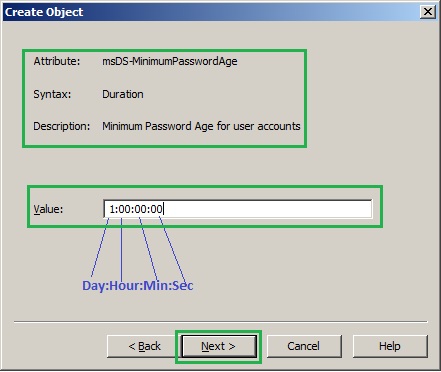
13. In the Create Object, Minimum password age for user accounts page, type 1:00:00:00. This value cannot be set to 0. A user cannot change the password within one day of a previous change. It follows the Days:Hours:Minutes:Seconds format (i.e. 1:00:00:00 equal to one day).
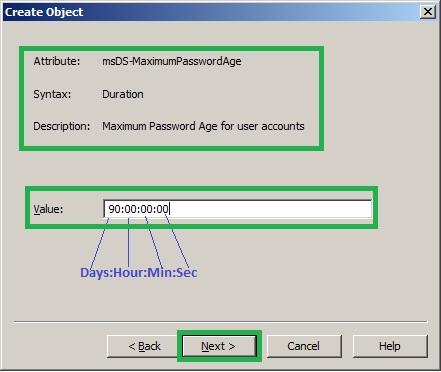
14. In the Create Object, Maximum password age for user accounts page, type 90:00:00:00 and click Next. The password must be changed every 90 days.
15. In the Create Object, Lockout threshold for lockout of user accounts page, type 8 and click Next. Eight invalid logons.
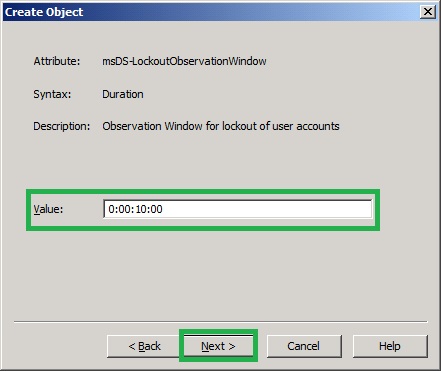
16. In the Create Object, Observation Windows for lockout of user accounts page, type 0:00:10:00 and click Next. Eight invalid logons specified by the previous attribute.
17. In the Create Object, Lockout duration for lockout user accounts page, type 0:00:10:00 and click Next.
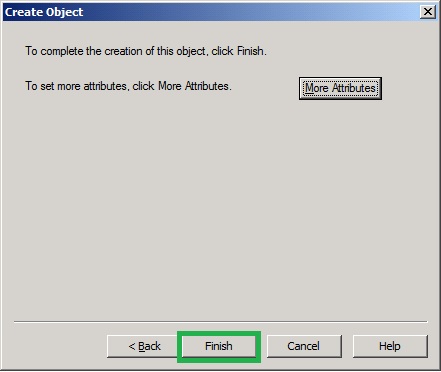
18. In the Create Object, instead of clicking Finish button, click on More Attributes button.
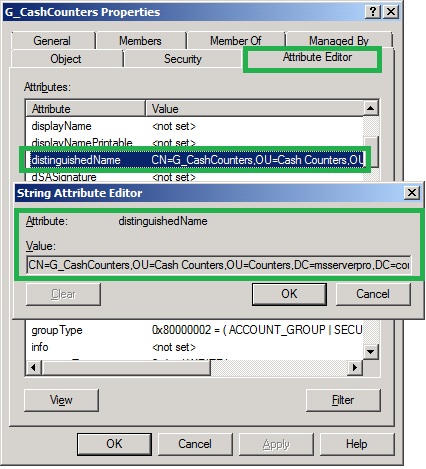
19. In the Select A Property To View list, select msDS-PSOAppliesTo and Enter the distinguished name of the G_CashCouters group and click Add and click OK.
Note: To view the distinguished name of the G_CashCouters , Open Active Directory Users and Computers, locate G_CashCounters, click Properties and click Attribute Editor. First ensure Advanced Features is selected.
20. Click Finish.
21. Test the settings by changing the password for the shreeyam account,who is the member of G_CashCounters,to a noncomplex, four-letter password such as simple.
Summary:
With Fine-Grained Password Policies in Windows Server 2008/2008 R2, we can create multiple password and lockout policies in the same domain. I hope this helps.
virtual dedicated server, computer servers, windows server 2003, server windows, dedicated server, low cost dedicated server, servers, dedicated hosting solutions, windows 2003 server, dedicated hosting server, windows dedicated server, linux server, dedicated windows server, canada dedicated server, server, amd server, blade server, small business server, cheap dedicated server, custom servers





















Hi
Thnx for a good explaination. I have created a fine grained password policy in 2008 R2 based on this manual. The purpose of my setup is have a user / usergroup with a pw policy that make the user pw to expire after 1 day.
An fine grained pw object in(test system):
test.local/System/Password Settings Container/finegrainedpwdpolicy
Attribute:
msDS-MaximumPasswordAge 1:00:00:00 (meaning 1 day, which I understand is the shortest value possible in this attribute
msDS-MaximumPasswordAge (none)
msDS-PSOAppliesTo CN=test2,OU=test,DC=local
Running the following cmd as admin:
net user /DOMAIN test2
……
Password last set 16.09.2016 05:24:27
Password expires 28.10.2016 05:24:27
Password changeable 17.09.2016 05:24:27
…
Last logon Never
I was expecting the password would expires in 1 day, not 42 day (as the default domain policy).
Please advice.
Best Regards
Audun